overleaf template galleryLaTeX templates and examples — Recent
Discover LaTeX templates and examples to help with everything from writing a journal article to using a specific LaTeX package.

This paper describes the use of the LATEX2e TRR.cls class file for setting papers to be submitted to Transportation Research Record: Journal of the Transportation Research Board, published by SAGE Publications: https://journals.sagepub.com/home/trr.

Assignment for Math Structure

This is the 2020 letterhead released by the Berkeley campus in Word + traditional Berkeley fonts.

"ModernCV" CV and Cover Letter LaTeX Template Version 1.1 (9/12/12) This template has been downloaded from: http://www.LaTeXTemplates.com Original author: Xavier Danaux (xdanaux@gmail.com) License: CC BY-NC-SA 3.0 (http://creativecommons.org/licenses/by-nc-sa/3.0/)

This is a letter template for the Aalto University School of Business.
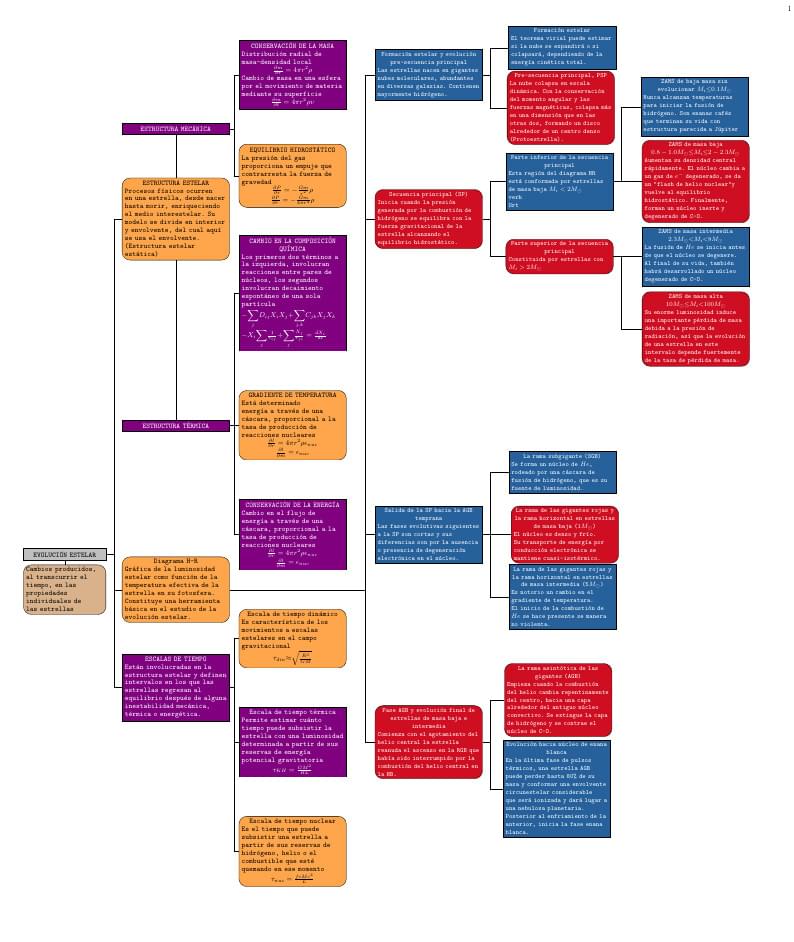
A horizontal stepped concept map.

Mohit Mehta's Résumé

phase1-AR.tex (use only for Archival Research and Theory proposals; use phase1-GO.tex for General Observer and Snapshot proposals and phase1-DD.tex for GO/DD proposals or use phase1-MC.tex for GO/MC rapid response proposals. HUBBLE SPACE TELESCOPE PHASE I ARCHIVAL & THEORETICAL RESEARCH PROPOSAL TEMPLATE FOR CYCLE 25 (2017) Version 1.0, January 2017 Guidelines and assistance Cycle 25 Announcement Web Page Please contact the STScI Help Desk if you need assistance with any aspect of proposing for and using HST. Either send e-mail to help@stsci.edu, or call 1-800-544-8125; from outside the United States, call [1] 410-338-1082.

Template for C240 Models of Computation Assessed Coursework 2 Contains macros for typesetting register machines in textual, graphical and encoded formats. Department of Computing, Imperial College London This work is released into the Public Domain.
\begin
Discover why over 25 million people worldwide trust Overleaf with their work.